On Saturday evening, Avast displayed a malware warning as I loaded a nytimes.com article. After some digging, here’s the malware I found.
Ad Delivery
nytimes.com article pages include an ad placement with the HTML DOM ID adxBigAd. From loading a few articles, they seem to rotate between a banner and an iframe. On this article, a 300x250 iframe was inlining this URL: tradenton.com slash ?id=21610438 (note: I don’t recommend visiting it, and URLs are not linked where possible).
A comment gave the campaign ID as Vonage01_1163613_nyt12, though it was obviously unrelated to Vonage. tradenton.com was registered Sept. 2, 2009, so it may have had a previous owner.
Injection
tradenton.com serves a 15-line HTML snipped containing this JavaScript:
As anyone who has looked at phishing links knows, this is nasty on a couple levels. It’s eval()‘ing escaped code, which is almost never needed to serve an ad. Note that the variable action_URL is defined but never used. After unescaping the code, this is what’s being run:
What’s served by harlingens.com slash includes02.js? Aha! The eval’ed JavaScript is requesting a second Javascript, which hits action_URL:
Malware
Now we’re talking. Requesting that action_UR on sex-and-the-city.cn actually serves a HTTP 302 Redirect to protection-check07.com slash 1/?sess=%3DGQx3jzwMi02MyZpcD0yMDguNzUuNTcuMTIxJnRpbWU9MTI1NjgwMI0MaQ%3DN. And we hit pay dirt. It’s a fake page for a non-existent antivirus app, which is actually malware. Titled “My computer Online Scan”, this page displays this JS alert:
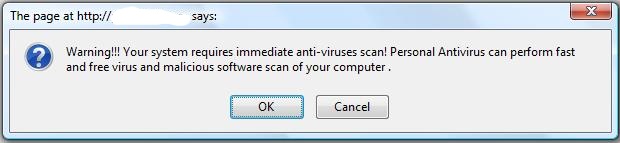
Then resizes the browser window into a full-screen application-style, as if it had become a virus scanner. Some highlights from the static content and JS on this page:
Dont close this window, if your want you PC to be protected.
353 trojans
You need to remove this threat as soon as possible!
Scan procedures finished.
431 Probably harmfull items was found!
Here’s a screen shot:
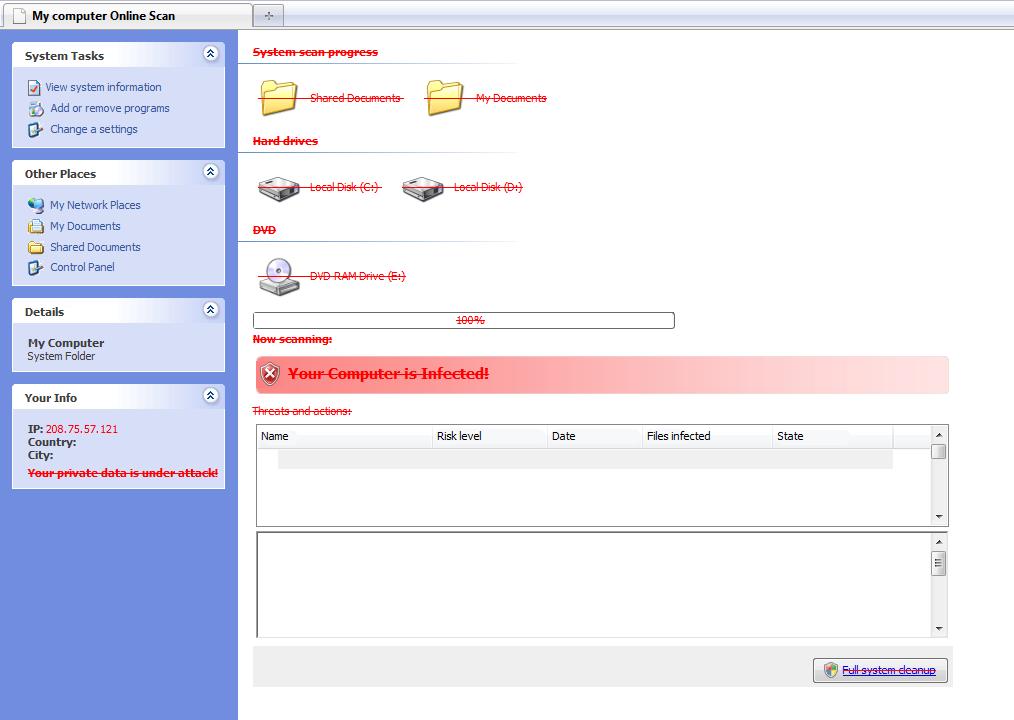
Here’s full HTML source in a gist viewer. As usual, these phishers haven’t sprung for spelling or grammar checkers.
The page also uses IP-based geocoding by inlining its own iframe called geoip.php, which has city-level granularity (though it was off by 1,000 miles for me). The “Full System Cleanup” link goes to /download.php?id=2006-63 on the same server, which serves a file called Scanner-b4ba2_2006-63.exe.
That redirects to /download/Scanner-b4ba2_2006-63.exe, a static file with the checksum 6c5b5669151337ca51ec45b1f5785d02. Running strings on this 167 KB program - too small for any virus scanner - has it requesting administrator privileges, though I haven’t done detailed forensics.
Notes
As of Sept. 12, 2009, tradenton.com and harlingens.com resolved to 212.117.166.69. sex-and-the-city.cn resolved to 94.102.48.29. protection-check07.com had 3 A records: 91.212.107.5, 94.102.51.26, 88.198.107.25. Also, I changed indentation and spacing for readability, so checksums on gist may not match source files.